Phishing Attacks on the Rise
Over the years, phishing attempts have presented a real issue for individuals and businesses. Sometimes the attempts are comical, but sometimes the attempts are highly sophisticated.
Despite the numerous warnings provided by experts, public awareness campaigns, and so on, phishing and email attacks are increasing. These attempts present a problem considering that more of our daily lives include online interaction and because so much of our information is now stored online.
I want to provide you with an actual case of phishing that happened to me recently. Normally, I delete and move on. However, I believe this one provides several clear warning signs that might be able to help you better protect yourself. Before I do, let’s clarify a few things.
phish·ing
noun
- The fraudulent practice of sending emails purporting to be from reputable companies to induce individuals to reveal personal information, such as passwords and credit card numbers.
Phishing attacks essentially break down into two categories
- Trying to trick the user into sharing sensitive information
- Getting the user to install malware.
Phishing and Email Fraud Statistics: 2019
According to Retruster.com
- The average financial cost of a data breach is $3.86m (IBM)
- Phishing accounts for 90% of data breaches
- 15% of people successfully phished will be targeted at least one more time within the year
- BEC scams accounted for over $12 billion in losses (FBI)
- Phishing attempts have grown 65% in the last year
- Around 1.5m new phishing sites are created each month (Webroot)
- 76% of businesses reported being a victim of a phishing attack in the last year
- 30% of phishing messages get opened by targeted users (Verizon)
Now that you know what you’re up against, let’s see what one of these attacks might look like. Here is an actual example of a phishing attack that happened to me. Can you pick out what is wrong?
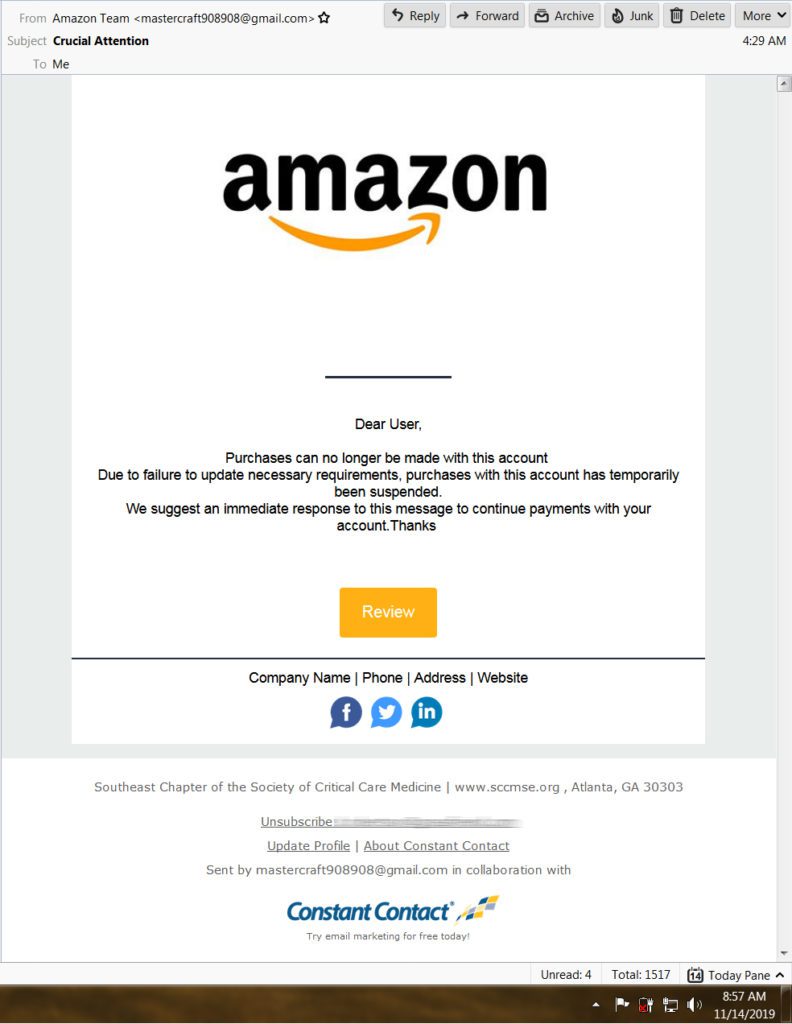
At first glance, this might seem convincing to some because you have some trusted names in the email. However, when you look at it, you’ll notice that this is one of those “comical” attacks. That’s why I couldn’t resist sharing it with my readers. I’ll break down all of the “clues” here in a moment, but first, I want to share some of the more common tacts used so you can keep from becoming a victim.
Phishing attacks come in many different forms. The one I presented here is called “The Billing Problem Tactic.” This is where the attacker tells you about a problem regarding your account and needs you to verify the information. This is usually done by “verifying” your information by putting it into their system.
Some other common tactics include:
- The Government Maneuver.
- The Expiration Date.
- The Virus or Compromised Account Scare.
- The Contest Winner.
- The Friendly Bank.
- The Victim.
- The IRS Communication
- The “Checkup.”
Some of these likely sound or look familiar, but there is an even more sinister tactic I need to share with you before we move on. It’s called “The Trusted Friend Tactic.” In the security world, it’s known as Spear-Phishing.
Spear-Phishing is currently the most successful and used tactic, as it accounts for roughly 91% of all tactics. In this one, the attacker acquires some of your basic data. This might include minor details regarding your friends, high school, hometown, places you frequently visit, and so on. Then the attacker pretends to be someone familiar to you, and they ask strategic questions to get your information. This would be an excellent opportunity to remind you of the DANGERS OF SOCIAL MEDIA POSTS.
So what are some ways we can quickly identify whether or not you are being “phished?” Here are a few tips.
Be suspicious of terrible grammar and punctuation errors.
Large companies invest a lot of time, energy, and money to put their best face forward. Furthermore, they usually have highly educated people checking over the things they send to their customers. This doesn’t mean they will not make mistakes, but they would likely be few and far between.
Be suspicious when your friends and family don’t sound like themselves
If your friends and family communicate with you over the internet, you likely have a good sense of how they do it. So if they suddenly don’t “sound” like themselves, if something seems remotely off, or if the correspondence seems out of place – it probably is. Give them a call to verify before you start answering probing questions.
Be suspicious when they ask for personal information.
If they do business with you, chances are pretty good that they don’t need your information. Furthermore, established companies know that asking you to send sensitive information over the net opens them up to liability. Therefore, if any information is sent, the chances are high that you will be speaking to someone directly while you do it.
Be suspicious of threats and consequences
Unfortunately, many people respond quickly to emotionally-based stimuli. Hackers know this, which is why some seek to scare you into acting quickly before you’ve had a chance to think it through. SLOW DOWN!
Be suspicious of “the AWESOME deal”
Similar to the previous heading, the fear of missing out on a great deal is just as powerful as the fear of trouble. That’s why hotel and vacation sites are always “one more left.” So if a deal seems too good to be true, it probably is. And if they need you to act right now, pass on it. Most of us don’t have the luck that would lead to a positive outcome on this one.
Be suspicious of urgent deadlines
If you receive an urgent deadline that doesn’t quite sit well or that you weren’t expecting, ALWAYS CALL using the information on the company’s established website – NOT THE EMAIL.
Be suspicious of big financial rewards
Let’s be honest… who in their right mind would send a stranger the opportunity for significant financial rewards without some serious investment? If such a scheme existed, it would likely be reserved for their friends and family and would probably be a pretty big secret. I promise you… a king in Kenya doesn’t care about you.
So now that you know a little bit more about what you’re looking for, can you pick out what was wrong with the email that I was sent? Here are the ones I caught…
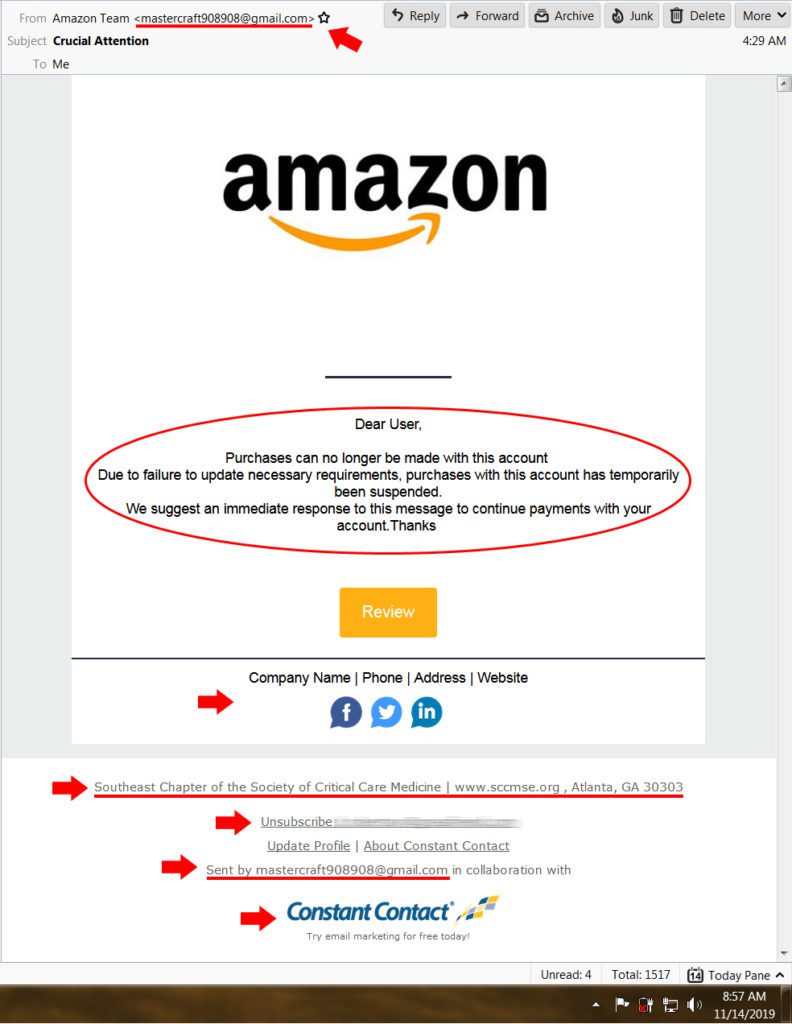
- The Amazon return email was from a Gmail account. For clarity, Google is a direct competitor of Amazon. It would be HIGHLY unlikely to get an email from Amazon using a Google product.
- Amazon normally addresses me by my name.
- Considering Amazon’s attention to detail, I know they normally don’t miss the grammar.
- Amazon is highly detailed (as opposed to vague) about any potential issue going on with any account.
- Company Name | Phone | Address | Website – instead of the actual information.
- What does the Southeast Chapter of the Society of Critical Care Medicine have to do with anything? Never heard of it before.
- Unsubscribe? (DON’T CLICK ON THIS EITHER)
- Amazon doesn’t need to use Constant Contact.
See what I mean? Sometimes phishing attacks are REALLY easy to identify (like this one), but sometimes they are more sophisticated. Just take a moment to review what you’ve been sent and give it some thought. If it doesn’t seem right, it probably isn’t.
THINK BEFORE YOU ACT!
Before I let you go, let’s look at the ones WAY TOO MANY fall for. These are not always “phishing” emails, but they do come in the email. Remember to always examine what you’re looking at and be careful of suspicious emails. They could be phishing, hacking, malware, virus, or anything else. Don’t take the chance.
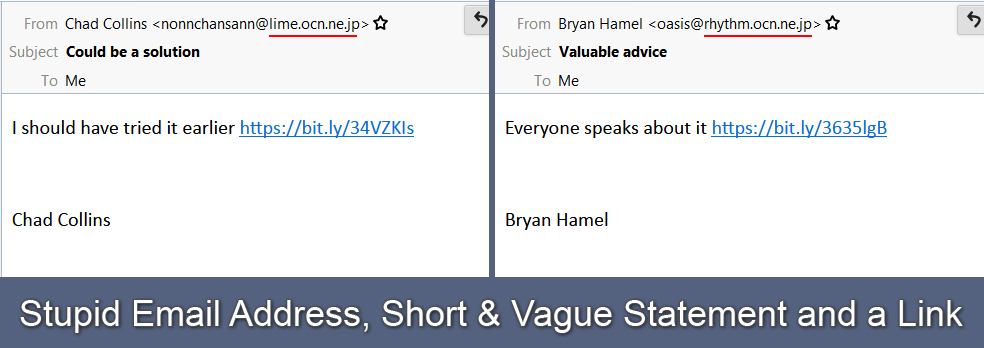
In these, the email address is typically messed up or doesn’t sound familiar. The email itself usually contains some vague statements along with a shortened link. DON’T CLICK ON THE LINK!
The funny thing is that these emails will typically hold a name you might be familiar with, like a friend or family member (usually because that person was silly enough to click on the link themselves). But the name is normally full. However, if you think about it, your friends and family wouldn’t have to tell you their last names, and if you examine their previous email, the chances are pretty good that their signature is different.
Here are two examples of some of the ones that have come through my email recently. One click and you’re compromised.
You might already be compromised if you’ve clicked on one of those links. That’s okay… lesson learned. You might be looking at the need for antivirus or antimalware in that case. So these are my top three favorite security programs this year. These are available on Amazon.com:




